Decisional Diffie–Hellman assumption
The decisional Diffie–Hellman (DDH) assumption is a computational hardness assumption about a certain problem involving discrete logarithms in cyclic groups. It is used as the basis to prove the security of many cryptographic protocols, most notably the ElGamal and Cramer–Shoup cryptosystems.
Contents |
Definition
Consider a (multiplicative) cyclic group 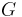 of order
of order 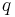 , and with generator
, and with generator 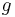 . The DDH assumption states that, given
. The DDH assumption states that, given 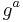 and
and 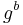 for randomly-chosen
for randomly-chosen 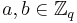 , the value
, the value 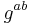 "looks like" a random element in
"looks like" a random element in 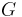 .
.
This intuitive notion is formally stated by saying that the following two probability distributions are computationally indistinguishable (in the security parameter 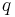 ):
):
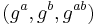 , where
, where 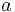 and
and 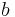 are randomly and independently chosen from
are randomly and independently chosen from 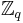 .
.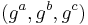 , where
, where 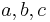 are randomly and independently chosen from
are randomly and independently chosen from 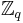 .
.
Triples of the first kind are often called DDH triples or DDH tuples.
Relation to other assumptions
The DDH assumption is related to the discrete log assumption. If it were possible to efficiently compute discrete logs in 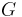 , then the DDH assumption would not hold in
, then the DDH assumption would not hold in 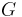 . Given
. Given 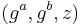 , one could efficiently decide whether
, one could efficiently decide whether 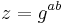 by first taking the discrete
by first taking the discrete 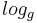 of
of 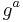 , and then comparing
, and then comparing 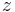 with
with 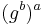 .
.
For this reason, DDH is considered a stronger assumption than discrete log, in the following sense: there are groups for which detecting DDH tuples is easy, but computing discrete logs is believed to be hard. Thus, requiring that the DDH assumption holds in a group is a more restricting requirement.
The DDH assumption is also related to the computational Diffie–Hellman assumption (CDH). If it were possible to efficiently compute 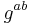 from
from 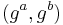 , then one could easily distinguish the two probability distributions above. Similar to above, DDH is considered a stronger assumption than CDH.
, then one could easily distinguish the two probability distributions above. Similar to above, DDH is considered a stronger assumption than CDH.
Other properties
The problem of detecting DDH tuples is random self-reducible, meaning, roughly, that if it is hard for even a small fraction of inputs, it is hard for almost all inputs; if it is easy for even a small fraction of inputs, it is easy for almost all inputs.
Groups for which DDH is assumed to hold
When using a cryptographic protocol whose security depends on the DDH assumption, it is important that the protocol is implemented using groups where DDH is believed to hold:
- The subgroup of
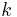 th residues modulo a prime
th residues modulo a prime 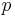 , where
, where 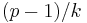 is also a large prime (also called a Schnorr group). For the case of
is also a large prime (also called a Schnorr group). For the case of 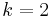 , this corresponds to the group of quadratic residues modulo a safe prime.
, this corresponds to the group of quadratic residues modulo a safe prime.
- The cyclic group of order
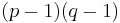 , where
, where 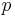 and
and 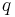 are safe primes.
are safe primes.
- A prime-order elliptic curve
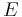 over the field
over the field 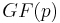 , where
, where 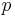 is prime, provided
is prime, provided 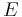 has large embedding degree.
has large embedding degree.
- A Jacobian of a hyper-elliptic curve over the field
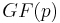 with a prime number of reduced divisors, where
with a prime number of reduced divisors, where 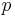 is prime, provided the Jacobian has large embedding degree.
is prime, provided the Jacobian has large embedding degree.
Importantly, the DDH assumption does not hold in the multiplicative group 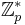 , where
, where 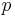 is prime. This is because given
is prime. This is because given 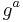 and
and 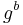 , one can efficiently compute the Legendre symbol of
, one can efficiently compute the Legendre symbol of 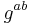 , giving a successful method to distinguish
, giving a successful method to distinguish 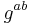 from a random group element.
from a random group element.
The DDH assumption does not hold on elliptic curves over 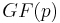 with small embedding degree (say, less than
with small embedding degree (say, less than 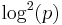 ), a class which includes supersingular elliptic curves. This is because the Weil pairing or Tate pairing can be used to solve the problem directly as follows: given
), a class which includes supersingular elliptic curves. This is because the Weil pairing or Tate pairing can be used to solve the problem directly as follows: given 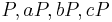 on such a curve, one can compute
on such a curve, one can compute 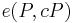 and
and 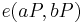 . By the bilinearity of the pairings, the two expressions are equal if and only if
. By the bilinearity of the pairings, the two expressions are equal if and only if 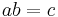 modulo the order of
modulo the order of 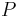 . If the embedding degree is large (say around the size of
. If the embedding degree is large (say around the size of 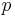 ) then the DDH assumption will still hold because the pairing cannot be computed. Even if the embedding degree is small, there are some subgroups of the curve in which the DDH assumption is believed to hold.
) then the DDH assumption will still hold because the pairing cannot be computed. Even if the embedding degree is small, there are some subgroups of the curve in which the DDH assumption is believed to hold.
See also
- Diffie–Hellman problem
- Diffie–Hellman key exchange
- Computational hardness assumptions
- XDH assumption
- Decisional Linear assumption
References
- Boneh, Dan (1998). "The Decision Diffie–Hellman Problem". Proceedings of the Third Algorithmic Number Theory Symposium. Lecture Notes in Computer Science 1423: 48–63. doi:10.1007/BFb0054851.
|
|||||||||||||||||||||||||||||